Introduction
The head of a company recently recieved an email from an external source. The link looked like it was from Bank of America about one of his corporate account logins. He clicked on the link and went to log in, but the screen kept saying that his information was incorrect. Later on, that corporate account was emptied into another account. The head of the company wants you to look at the email he received and figure out whether it is to blame for what happened.
Glossary
When analyzing an email, you should begin by looking at the email header. The email header is almost like an email’s passport, and it will let you figure out where the email came from and the steps it took along the way. There are a few key parts to an email header, and they are as follows:
- This is the person who sent the email. Sometimes it is clear that the email address is fake; for example, there may be a small misspelling of the real sender’s email.
- Always check the IP address if you believe phishing has occurred.
- This is the person who received the email and is the target of a possible phishing attempt.
- In a situation like this, the email is likely “whaling.” This is when a believable, but false, email is sent to a CEO or upper management in a company to gain access to credentials.
- This is the exchange sender and is generally a mail client server.
- This is the exchange receiver and is generally a mail client server.
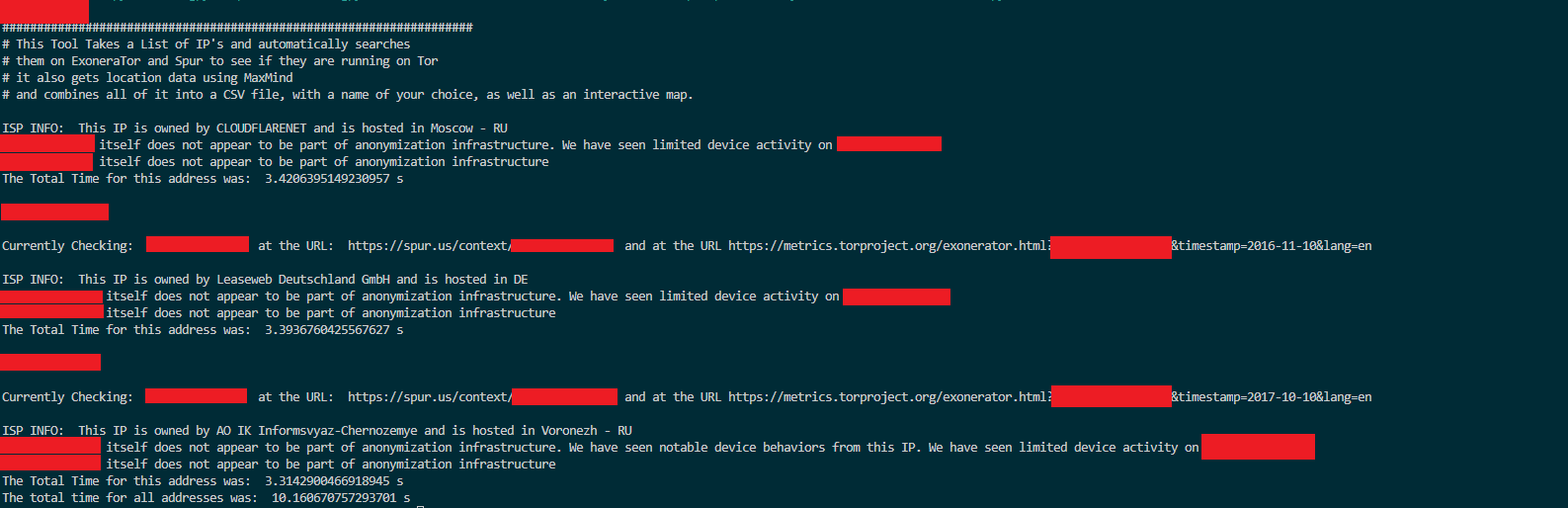
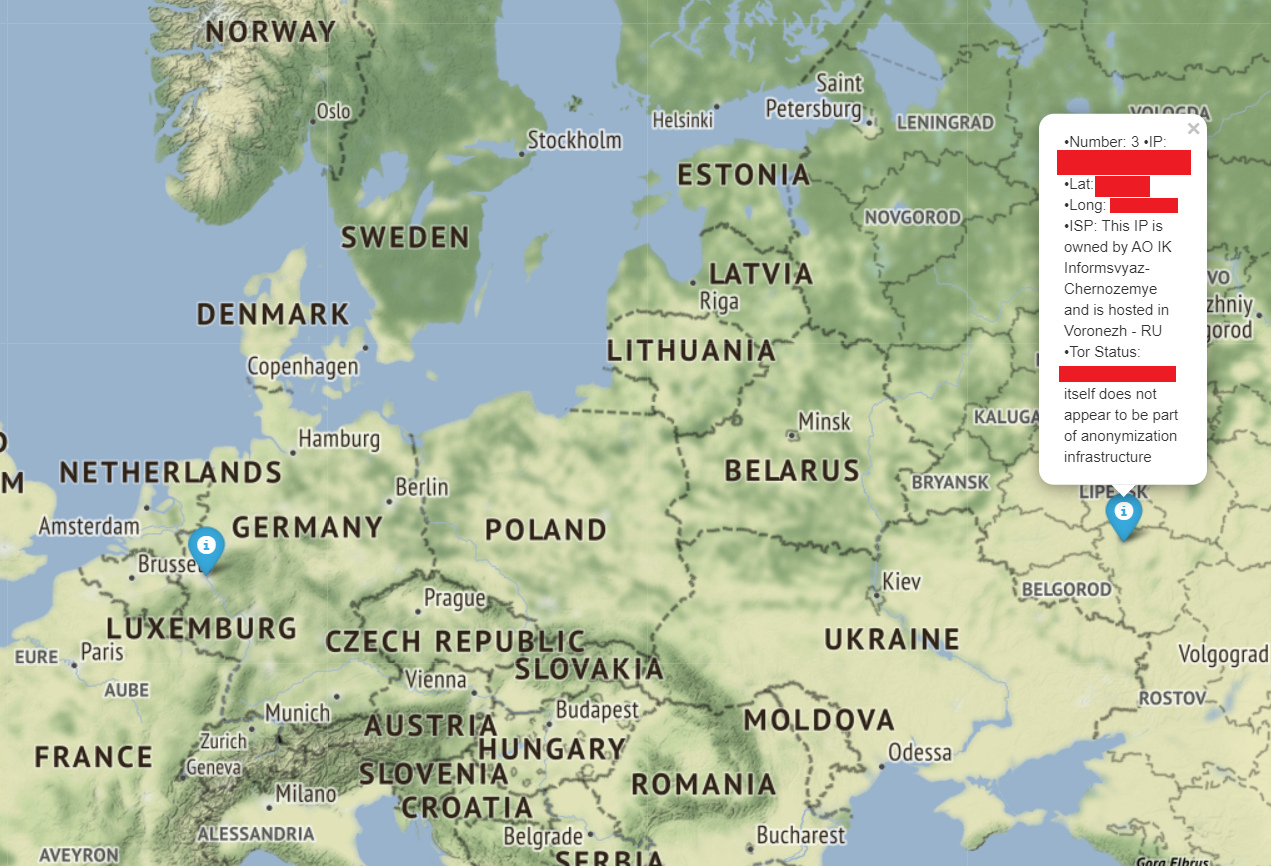
- IP addresses are relatively unique identifiers for systems connected to the internet. They are important for attributing behavior within a certain time to an actor online.
- IP Resolution is the process of taking an IP and getting information back on whom owns it, who it is assigned to, the location, and more.
Analyzing Email Headers
Following Up